Chrome is visually penalizing long-lived SHA1 HTTPS certificates. The information about it is a bit scattered around so I'm writing this to provide a complete and hopefully correct overview.
Just give me the tl;dr
If your certificate is expiring after Dec 2015 and:
- it's signed with SHA1, or
- one of the intermediates is signed with SHA1
then respectively get your certificate reissued ASAP or download the SHA256 version of the intermediate.
What's the timeline?
The official timeline is here but you have to replace "41" with "42".
Basically, version 42 of Chrome implements the last step of the restrictions, affecting certificates valid past 2015.
Version 42 is the current beta version, and should be promoted to stable (what everybody runs) on April 14th.
No more changes will happen after v42.
What happens if I'm affected?
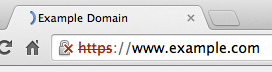
If your certificate expires in 2016, you'll get this "minor errors" indication

Note that the above is true in the current stable already.
If your certificate expires past 2016, then you'll get the "broken https" indication
In any case, no warning screen will be shown and no connection will be blocked.
How do I check?
Run the Qualys SSL Test and check the "Certification paths" sections for "WEAK SIGNATURE" warnings. The test will also warn you in the main report box.
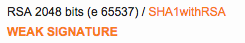
Remember that it's only a problem if the certificate expires in 2016 or later. If it expires in 2015 you can worry about it next time you renew.
What about subresources, like scripts?
Subresources (like <script src=...>) from "red lock" (having SHA1 certs and expiring past 2016) domains will be treated as "active mixed content", so they will not load (or cause the parent site to display a "minor errors" indication for <img>).
It looks like v42 does not actually enforce this, but it's going to happen.
How do I fix this?
Your CA surely has instructions for you. Here are some links.
If the problem is an intermediate certificate you don't even need to have your certificate reissued.
Why are they doing this? Isn't SHA1 better than plain HTTP?
This is my sole opinion. Not Google's or my employer's.
The keyword here is long-lived. A big problem with online security is having to support old broken stuff coughSSLv3cough because there are wide deployements.
That often lowers the security of everyone else using better cryptography because of downgrade attacks, and this is not acceptable. So yeah, HTTP is worse, but at least it does not damage other HTTPS sites.
Also, think of the alternative. It would be accepting SHA1 certificates as good in 2017, when they might be as brittle as MD5. Or having to do all this dance with a week's notice because some breakthrough research gets published.
The web PKI needs to stay up to date.
Other questions?
I'm @FiloSottile on Twitter.
Thanks to Ryan Sleevi and Chris Palmer of the Chrome Security Team for helping me get this right.
Note that I'm in no way affiliated with Google or the Chrome Security Team.
