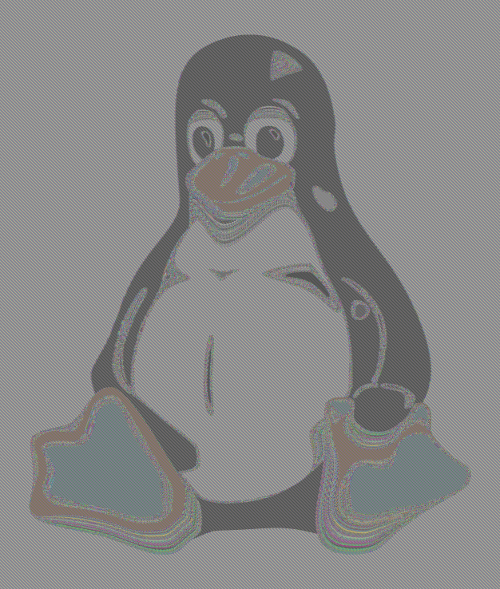
The ECB Penguin

This is an image that has become kind of a cultural icon in the cryptography and InfoSec community. I’m speaking about “the penguin”, a picture of the Tux Linux mascot encrypted with a block cipher in ECB mode that still shows clearly the outline of the original.
.@solardiz @ErrataRob ECB mode strikes again, I see. It's hard to believe there's anyone left who hasn't seen the penguin.
— Andrea (@puellavulnerata) November 3, 2013
ECB
You have a cipher, that with a key will encrypt 16 bytes of data. And you have some data, that is more than 16 bytes. So you have a problem. Well, ECB is the wrong solution to that problem: you just encrypt each 16-bytes block separately.
Why is it wrong? Because this way blocks that were equal before encryption will remain equal also after! And this will lead to all kinds of unwanted consequences.
One good example is the recent Adobe passwords crossword game but the best visualization of the concept is him, the penguin!
The original
The original image has been created by User:Lunkwill of en.wikipedia in 2004 and added to the page “Block cipher mode of operation” with this edit.
It has even been proposed as a Wikipedia featured picture.
Nothing more is known about the original. I wrote an email to the author, and I will update the blog post if he replies.
Edit 2019: I just noticed that the author got back to me a few months later.
As I recall, my advisor at the time mentioned that he had seen such an image in a talk. I couldn’t find it anywhere, so I created my own. As I recall, I converted TUX into a bitmap format like PGM, encrypted with some key I don’t remember and then swapped a valid header back in. So it’s a lot like the one you made. Lunkwill (talk) 01:30, 3 May 2014 (UTC)
My take at it
The picture is amazing, but rather low quality even for screen, let alone for printing. So, I decided to generate my own.
First thing needed was an image format where the pixels were represented sequentially as plain bytes, without any compression, and possibly with a simple header. The perfect candidate turned out to be the PPM binary format, part of the Netpbm spec. (It is just basically a ASCII header and then a sequence of 3-bytes RGB representations of the pixels.)
Here is the process:
# First convert the Tux to PPM with Gimp
# Then take the header apart
head -n 4 Tux.ppm > header.txt
tail -n +5 Tux.ppm > body.bin
# Then encrypt with ECB (experiment with some different keys)
openssl enc -aes-128-ecb -nosalt -pass pass:"ANNA" -in body.bin -out body.ecb.bin
# And finally put the result together and convert to some better format with Gimp
cat header.txt body.ecb.bin > Tux.ecb.ppm
And the result! Click for the original. It makes for a great nerdy office decoration, much like “Crypto Safety Procedures”!
Bonus: pop art
Also, the color combinations spawning from the different keys reminded me of the Marilyn Monroe by Andy Warhol, so… Poster!

 The images are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
The images are licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.